.Cloud security is becoming increasingly crucial as more business is done online. The COVID-19 epidemic significantly expedited the adoption of virtual tools and platforms. That is leading to a profound change in the way that enterprises throughout the world do business.
As businesses increasingly rely on cloud technologies, extra elements are now in play. Cloud computing activities expand, and security breaches become more costly with cloud security managed services. Preventionist mitigation is, therefore, more significant. The best practices for access and monitoring, disaster recovery procedures, and regulatory compliance must all be specified and balanced in order to proactively increase your cloud security (particularly in the healthcare and financial services verticals).
Security is a joint obligation between the customer and Amazon Web Services (AWS) with this provider. AWS is in charge of cloud security, which includes both software and hardware, while the customer is in charge of cloud security, including identity and access management, firewall setting, and guaranteeing the privacy of client data.
Teams have three main alternatives when it comes to security: try to handle security entirely on their own, use AWS services directly, or engage with a managed cloud service provider to make sure the best services are used appropriately.
Getting cloud security managed services is difficult
Many firms lack the skills necessary for cloud security, especially when bad actors use more advanced methods. It can be difficult and time-consuming to align the appropriate skill and knowledge resources, particularly when there are significant security gaps. You simply cannot develop internal competence in cloud security overnight.
It can be challenging to get expert talent, and the challenge increases if you don’t already have inside experts who can onboard security professionals under a more comprehensive strategic strategy. It can be difficult to find an individual who fulfils your expectations due to the shortage of qualified cybersecurity workers. According to Esmi research, just 48 competent individuals are available for every 100 active job advertisements, leaving half of those organisations’ openings unfilled.
You shouldn’t, however, attempt to learn about cloud security as you go. Too many unknowns and edge cases exist. Additionally, developing the necessary skills takes time. You can’t afford to keep making the same mistakes because even a small security violation can bankrupt a firm.
You Can’t Afford To Choose The Wrong Security
Attackers are more motivated to look for vulnerabilities in cloud infrastructure because of the global growth of online commerce. Errors that provide hackers access are a major source of security issues.
Report for Summer 2020 by Accurics In 93 percent of the cloud installations that were examined, it was discovered by The State of DevSecOps that cloud storage services were frequently misconfigured. Additionally, most installations had at least one network exposure where a security group was left unprotected. In the previous two years, 30 billion records have been exposed due to just these two techniques being at the centre of over 200 breaches.
Additionally costly are security lapses. According to Gartner, the typical cost of IT downtime (which might happen as a result of a breach) can cost up to $5,600 per minute. Organizations simply cannot afford to make security mistakes.
Security vulnerabilities also harm a company’s reputation, which is very important. Consumer trust that has been damaged by a security breach or data loss is difficult to recover.
What’s more for you about cloud security managed services?
In this blog, you will also come how AWS monitors the accounts and applications running in its environment. We will discuss some account and application security tools provided by AWS. Big company owners acknowledge the fact that using virtual, physical, private cloud, and public cloud computing combination is necessary for their success in the modern world. AWS security tools are the best solution for you. It offers you ample security tools for both your accounts and applications or services that you can use according to your need and preference.
AWS is highly focused on the security of its environment as cybersecurity is one of the major concerns when we are running our IT networks. We will discuss how these tools are helping you in the running of your AWS environment. also the discussion of these tools is going to improve your cybersecurity and take it to the next level. We will also review AWS account security versus application and service security.
Account Security Versus Application And cloud security managed services
AWS security tools cater to both the perimeters whether it is account security or application and service security. It is not wrong if we say that an AWS account acts as an attack vector. Why, because its data and resources are accessible through public API (application programming interface). So there is a dire need to implement high security to the accounts. The strategies implemented by AWS help in preventing the leakage of data to the public. For this, AWS uses a secure identity and access management strategy. so that data is not leaked to the public by offering you access patterns and configured permissions. It also keeps a record of your actions for audit and compliance purposes.
Applications and services running in the AWS environment are prone to several sorts of threats. such as attacks from Cross-site scripting (XSS), SQL injection, brute force, and distributed denial-of-service (DDoS). They attack to slow down your service and application and threaten security as well. Without the provision of adequate management, there are higher chances of leakage of your sensitive information to the public. The strategies implemented by AWS help in preventing the leakage of data to the public. Applications and services running in the AWS environment can be exposed to several sorts of threats and attacks. For this purpose, AWS uses a secured access management strategy. so that data is not leaked to the public by offering you access patterns and configured permissions. It also keeps a record of your actions for audit and compliance purposes.
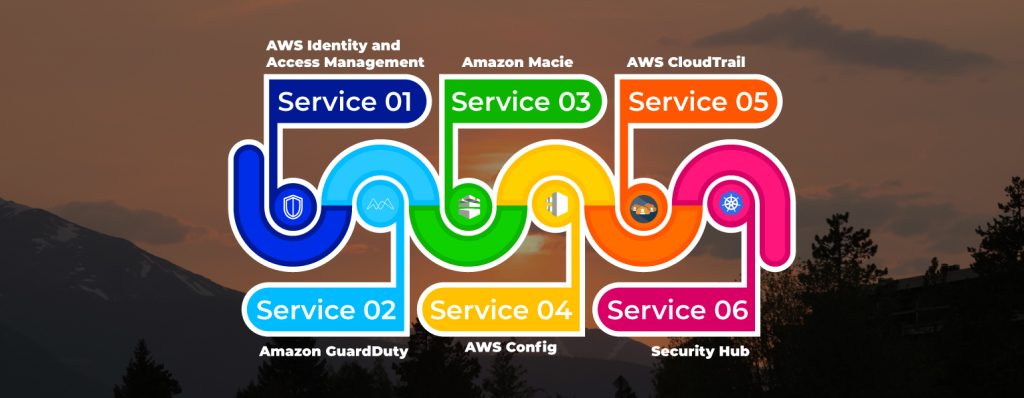
Six AWS Account Security Tools enable you to keep your accounts secure from the loss or leakage of data.
Top 6 Cloud Security Managed Services
1. AWS Identity and Access Management (IAM)
The first account security tool that we will talk about is AWS Identity and Access Management (IAM), it is an important security tool, it provides its customers with controlled access. It provides you with the right to give permission to your users for accessing the resources. You can use AWS IAM for testing and troubleshooting the permission extent that you have assigned to your clients and users following the rule of least privileged of the IAM configuration.
This helps in minimizing the chances of attack from outside. AWS IAM provides you with multi-factor authentication to secure the access of the user.
2. Amazon GuardDuty
If we talk about Amazon Guard Duty, it detects malicious activities prevailing in your environment by the use of machine learning. It can also detect abnormalities in access patterns. The price of Amazon GuardDuty installation and maintenance usually increases linearly, meaning that the price will also increase when you are increasing your AWS environment. It is difficult to predict the exact cost as it varies with the amount of data being managed.
3. Amazon Macie
Amazon Macie will notify you whenever your data or your S3 bucket is accessible to the public or is unencrypted. It alerts you whenever your AWS account is shared with outsiders.Amazon Macie is concerned with protecting your confidential or sensitive data present in the S3 buckets in the AWS environment. It first figures out where your sensitive data is, then identifies that data and makes it secure.
The number of S3 buckets and the amount of data that Macie is monitoring are the determining factors of Amazon Macie’s pricing. So we can say that its pricing structure is dependent on the amount of data being monitored.
4. AWS Config
AWS Config helps you to record and evaluate your AWS resource configuration continuously. It conducts a continuous evaluation of your AWS resources and keeps records of all the changes that you have made in your resources. AWS Config requires configuration per region, so it must be configured in all regions so that all the resources can be recorded and evaluated continuously.
It is very important for the smooth running of your IT resources in the AWS environment. For E2C instances, it is necessary that all the volumes should be encrypted, so if any volume is not encrypted AWS Config encrypts it or deletes it accordingly. This is one of the best choices for you whenever we talk about AWS account security tools.
5. AWS CloudTrail
AWS CloudTrail was introduced in 2017. It will help you to manage all your accounts within your organization. If you want to track all the activities that you are performing in the AWS environment then it would be the best option to use AWS CloudTrail for that purpose. As it tracks all the activities performed in your AWS environment.
This is an important tool as it keeps a record of all your activities and events so that you can view all your activities. This helps you in maintaining a secured AWS environment. It notifies you whenever an abnormal activity is done in your AWS environment.
6. Security Hub
Lastly, Security Hub is one of the most important tools for account security. As it combines all the above services, the security hub functions by combining the above services in a centralized and unified way. It collects and combines all the data gathered from your AWS accounts functioning in all the regions. Then it provides you with a complete view of the AWS security posture
The most important feature offered by the security hub is that supports the security standards recognized by the industry such as the Payment Card Industry Data Security and CIS AWS Foundations Benchmark.
These were the AWS account security tools that help you in managing. also assists you keeping your accounts secure and safe from outsiders’ attacks or leakage of your important data.
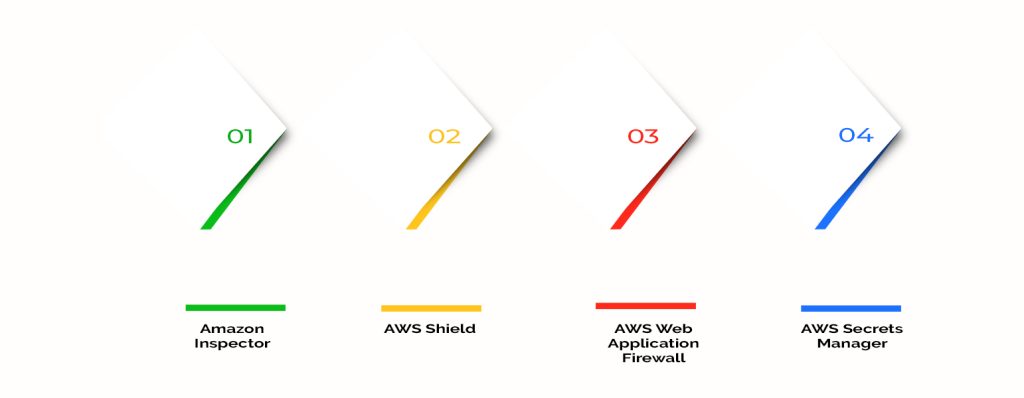
Best cloud security managed services Tools
As we have discussed the AWS account security tools that you can use for your AWS accounts. Now let’s discuss the AWS application and services security tools.
The following are the top 4 AWS application and services security tools.
1. Amazon Inspector
The first application security tool that we will discuss is Amazon Inspector. It protects your application by conducting a security assessment of all the AWS services and applications present in the E2C instances.
Amazon Inspector helps you in generating a detailed report consisting of all the security findings. Therefore by installing it, you will be able to monitor your application and its security effectively with ease.
2. AWS Shield
AWS Shield is also known for providing high-quality protection against distributed denial-of-service attacks. It shields your application against such attacks led by DDoS.AWS Shield guards and shields your applications running in the AWS environment. It protects your applications from malicious activities from the outside. AWS shield helps you in managing the security of your applications within your system.
3. AWS Web Application Firewall
If you are looking for an adequate tool that can protect your AWS applications with efficiency and ease. then it is one of the best tools for you to use. WAF or AWS Web Application Firewall is also a well-known and famous security tool for the protection of your AWS applications. It protects the applications and blocks access of your application to outsiders.
You can use this app as it will help you in improving your security posture because it restricts the number of users per IP for enhanced security of the application and protects your application from outside attacks.
4. AWS Secrets Manager
AWS Secrets Manager is an important tool for application security. It helps you in storing and retrieving all your private information such as your important certificates, tokens, and database credentials. You can opt for AWS Secrets Manager. AWS Secrets Manager is responsible for creating, deleting, updating, and retrieving secrets. It is a managed service that helps you in restoring and retrieve your private information. So if you want to store and retrieve your confidential or private data and information, AWS Secrets Manager is the best option for you to choose.
Conclusion
To sum up, AWS is known for its cloud security managed services. It provides its users with a lot of security services which makes it difficult for you to choose one among them. AWS offers a wide range of security services for you now it’s up to you to choose the most suitable one according to your needs.
If you wish to learn more about our Managed Detection and Response (MDR) service. feel free to contact us and discover how AWS security services can help you in improving your security posture. click here!
Read more: The Ultimate Guide Of Migrating Hdp Cluster To Amazon Emr